
The demand for online security has never been greater. What was once a luxury item has now become a necessary component for your online presence. Whether you're a company conducting business online or a consumer who stores their personal info online, there is a potential risk. With an ever widening range of online attacks, you absolutely need to protect your property. =
Distributed Denial of Service (DDoS) is a digital attack that attempts to disable any online service by sending an overwhelming amount of traffic from multiple sources, also known as 'Botnets". Though these attacks do harm, they are not targeting to expose or steal any personal information, but rather to overpower a service through the hosting server, making it unavailable to it's users. Over 2000 DDoS attacks are observed daily with one-third of all online downtime complications resulting from DDoS bombardment.
These attacks can be disguised in many shapes and sizes; however, each strike falls under one of the three core categories:
Volumetric
In a volume-based attack (ICMP), the bandwidth of a network/service is affected and flooded.
Protocol
Protocol attacks are aimed at saturating networks resources by sending open requests (Pings of Death).
Application
An application violation (Slowloris) targets the hypertext transfer protocol with the conclusional outcome of crashing the server.
The process of recovering from a DDoS attack can take hours to days to weeks; all depending on the time length of the strike. All businesses and consumers should take the precaution of purchasing an anti-DDoS service to insure your IT safety.
Here are our top 5 DDoS Protection Selections:
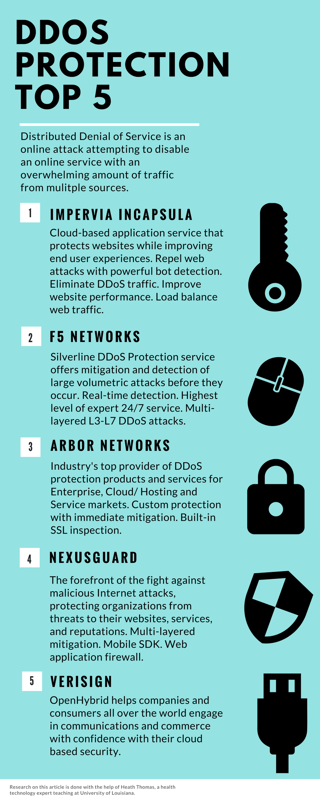
There is just too much on the line when it comes to protecting your online assets. Just remember that one of these attacks has the potential to destroy all the hard work you’ve put in to your online presence. Beat the botnets to the punch, and take immediate action by purchasing a protective service.
Related Blog:
IS YOUR CYBERSECURITY AS SOLID AS YOUR BUILDING SECURITY?




