When thinking about security for your business, you’ve no doubt seen to it that your office building is well-protected. You’ve got an an alarm system, security cameras and/or a guard posted at the front at your building.
But there is another vulnerability that you might be overlooking that could do way more damage than anything lurking outside.
Increasing Costs of Invisible Threats
The alarming acceleration in the growth of cybercrime is making it difficult for analysts to zero in on what the real cost to businesses is, but it’s reaching record levels. One of the latest findings, according to the IBM Cost of Data Breach Summary is that attacks are growing in both volume and sophistication, increasing overall by 64% in 2015 from 2014, and steadily rising.
The higher complexity of these recent attacks are costing companies more than ever before. The study found that each compromised record can cost $158, with an even higher cost impact in regulated industries like healthcare - a whopping $355 per record. That can add up astronomically when there are thousands of entries.
It’s not Just About Virus Protection Anymore
These sophisticated attacks are getting smarter and stealthier, and can wreck havoc on your business unless you’ve got someone watching specifically for them. An undetected breach, even it it's only for a short period of time, can result in a potentially severe impact to both your business and your customers.. Each minute that the data remains vulnerable, the costs of containing the hack skyrocket.
The only way to mitigate the damage is to have a cyber security response team at the ready to perform incident forensics, stop data leakage, and report the breach to the appropriate agencies, partners, legal and customers immediately. A surprising amount of organizations, even ones in critical sectors like energy and utilities, are not prepared enough to deal with a serious attack.
An Ounce of Prevention…
With the cost of the average data breach climbing up to $4 million an incident, the only offense is to build the strongest defense and apply enterprise risk management. Given the growth and strength of the threats, security breaches have to be factored into the cost of doing business at this point. Investing in cybersecurity failsafes before you face a catastrophic problem is crucial, as it may be it’s too costly and difficult to play catch-up after an attack.
Calling in the Cavalry
Following increased reports of worsening high profile attacks, more and more companies have decided to take the proactive route, and are turning their ships in the right direction and making it a priority to recruit the right cybersecurity talent to properly protect their critical data.
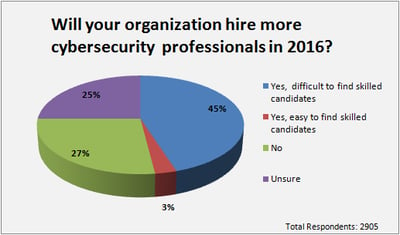
Source: IT NEXT
No one wants to be the next Home Depot, (that recently agreed to pay at least $19 million to 50 million cardholders) or the Democratic National Committee, whose computers got infiltrated and combed for months only to have sensitive campaign information leaked, or completely lose the ability to provide service to customers, so what is a company to do?
According to Radware, Organizations under threat should consider:
- A cyber security emergency response plan that includes an emergency response team and process in place.
- Protecting its infrastructure from multi-vector attacks that can saturate the Internet pipe.
- Including on-premise detection and mitigation with cloud-based protection for volumetric attacks.
- Providing protection against sophisticated web-based attacks and website intrusions to prevent defacement and information theft.
- Monitoring security alerts and examine triggers carefully. Tune existing policies to allow identification of real threats if and when they occur.
If you’re considering adding cybersecurity experts to your organization, you should:
- Find the right expert for your business size and function. If you’re smaller, you can consider someone that fits a few classifications. If you’re larger, be prepared to go for a more specialized team if you need to protect a wealth of critical personal information.
- Don't delay beginning your search. Some organizations are reporting that it can take 3-5 months to fill a senior position in some sectors.
- Get help recruiting the perfect candidate, someone who fits what your business needs right now, as well as who seeks to adapt, keep up certifications and will grow as you and the tech changes.
J. Patrick and Associates serves Information Technology firms that are looking to improve or expand their teams in mission-critical functions, where the success of the firm is highly dependent on the quality of certain hires. If your goal is to build a star cybersecurity team, contact us today: