“There is a zero-percent unemployment rate in cybersecurity and the opportunities in this field are endless” - Robert Herjavec, CEO at Herjavec Group
Cybersecurity Ventures predicts there will be 3.5 million unfulfilled job positions by the year 2025. Due to the dramatic rise of cybercrime, the malicious malware epidemic, and the increasing amount of severity attacks on consumers, businesses, and government institutions; cyber security is predicted to cost trillions of dollars annually by 2025.
In essence, bad news for the security of our information is good news for sales engineer employment. And where there's a boom, there's a demand for talent. One field that's feeling the full effects of this expansion is cybersecurity sales engineers.
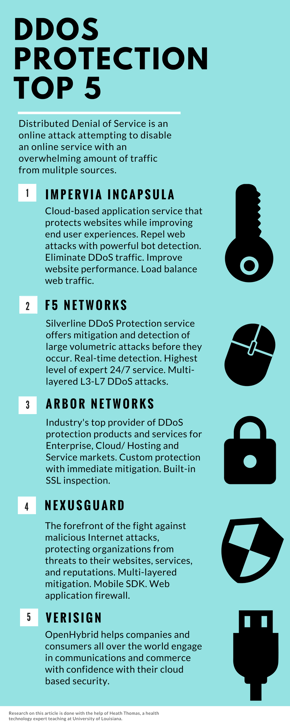
Cyber Security Sales Salary
With an increase in cyber security sales engineers, demand comes an increase in salary range. In 2022, the average American Cyber Security Sales Engineer's salary was between $80-$150K, with experienced professionals averaging over $120K. And in an environment where talent is at a premium, and the demand is outpacing the supply; candidates who are in the job market often are fielding competing offers, as well as counter-offers from their current employers.
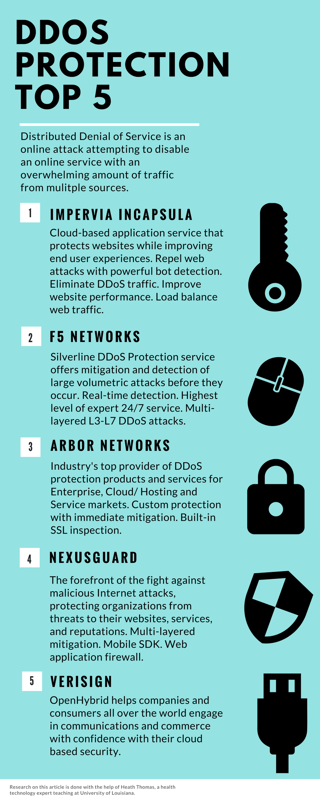
Cyber Security Sales Engineer Path
What the increase of hiring means is, if you're in cyber security presales, you have the opportunity to exercise agency over your career by taking the offers that you feel stand to most enrich and add value to your career trajectory.
Hiring Managers
If you're a hiring manager charged with hiring cyber sales engineers, you already know that the competition for talent is fierce. You also know that you might have to push your budget to get the level of talent you need to keep your company's and/or your customer's data safe. And you probably also understand there's tremendous value in interviewing candidates even when you don't have an immediate opening. But there are a few other key issues to keep in mind.
Lose the Checklist
When you're faced with a competitive market and top talent comes at a premium, you have to be willing to look beyond your checklist. The best candidate may not carry all the certifications you want to see, or they might carry ones you never considered important. They might come from a different sector or not have the years experience you're looking for, but the overabundance of open cyber security sales engineer jobs needs to be filled. This means that you need to develop a technique for evaluating the kinds of non-technical skill sets that will stand you in good stead when making a hiring decision.
Understand the Power of Soft Skills
As the bridge between the technology and the customer, a sales engineer's ability to manage and communicate effectively with customers needs to be a prime consideration. Since they are in daily contact with customers, they are your eyes and ears in the field, and having someone who is an agile communicator of human experience (as well as technical expertise) is invaluable to you. While you will directly experience a candidate's interpersonal aptitude in an interview, you can also ascertain the nature and extent of their skills by having them complete a respected psychometric exam like the O.C.E.A.N./Big 5 personality indicator.
Hone Your Game
And speaking of soft skills, in order to attract the best talent, you need to have a company culture in place that both values and invests in their employees. We already know that the best retention and recruiting tool is to make employees and candidates feel valued. Determine what your ideal candidate would need in order to feel like a valued member of your team and actively develop those aspects of your business. Always keep in mind that--now more than ever--the proverbial "ball" is in candidates' courts. Top talent will carefully weigh the prospect of working on your team against that of working for your competitors.
When you're hunting for top talent in a crowded field, always make sure that you have the best position on offer.
Looking for a cyber security sales engineer to join your sales team? Click Here, and a recruiter will reach out to you within 24 hours.
Are you looking for an account manager, pre-sales, post-sales, systems engineer, sales executive, sales manager, solutions engineering, or either security systems or security services position? Click Here and search our current openings!