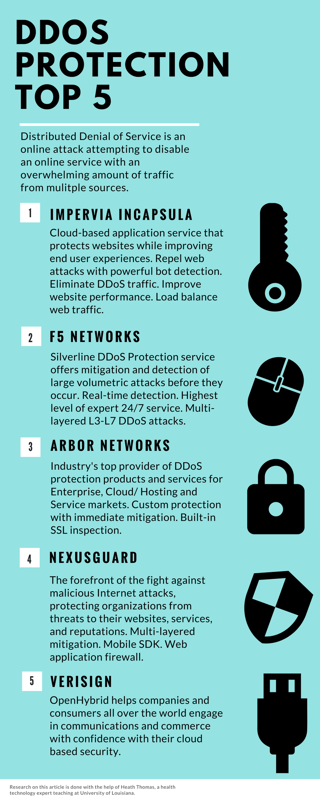
IoT Security: Protect your product and your customers
Think of IoT as the gateway between the digital and physical worlds. Products are being created with pattern recognition and monitoring sensors providing valuable data that can be applied for the benefit of its users and producers. This market will continue to expand over the next 10 years with companies connecting more and more devices. However, with the connection of so many devices, also comes an increase in the number of entry points for potential hackers.
Since IoT is relatively new to the market, devices often lack basic security measures (Communication Encryption). Researchers have shown that many IoT device manufacturers and service providers are failing to implement common security measures in their products. Reports have surfaced exhibiting the increase in programmers hacking into products, ranging from baby monitors to self-driven cars.
Standard security technologies (SSL.SSH) are no longer enough when it comes to safeguarding your IoT devices. The only way to stay ahead of the cyber terrorists is to embed integrated firewalls directly within the protocol stack at the link-layer- configured with a specific set of rules on what communication is and isn't allowed.
These firewalls are necessary to stop the cyber-attacks before they begin.
Failing to implement a strong security protocol will result in:
Loss of Customer Trust
Customers don't want to worry about having their personal information exploited. We all remember what happened to Target.
Increase of Expenses
After being hacked, there is a mass amount of damage control to attend too. That’s a pricey expenditure.
Competition Head Start
To compete in the market, you must offer benefits that your opponents cannot. Don't let your competition leave you in the dust.
Firewall_1.png
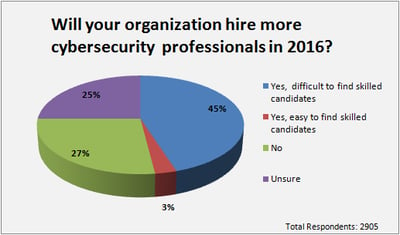
Investment in securing IoT machinery is going to drastically increase from now till 2020. If you're in the market, it's time to check your